While taking a break from studying for the Core Exam, I stumbled upon this 2016 document from Microsoft about password security (yes, in some circles that is considered “taking a break”).
As radiologists, every day we are being asked to type in some sort of authentication username and password at work. Every other week, we’re asked to change passwords for security reasons. Every month, we forget one of those 23 passwords we’ve created over the past 3 years for the VA or another affiliated hospital, or some software you’ve not used for a while, or even just plain forgot.
So all radiologists should know a few things about password security, and this document is a reasonable place to start because many radiology departments use Microsoft products. I also like this document for a number of other reasons.
They cited other interesting work on security
Do people actually somehow expect me to remember 23 different passwords, all with complex symbols and numbers? If someone asks you to come up with a really long password, at what point do users just stop making good passwords (“fourfourfourfour” and “passwordpassword” are among actual examples of 16-letter passwords)?
They realized nobody is going to read the whole thing
It’s a research paper. And yet, there is an executive summary with pictures. Well done, Microsoft.
Someone finally realized that the only thing people like about passwords is reading a research paper on passwords.
There’s a reference to web comics XKCD
The document actually makes reference to this XKCD web comic which involves the use of “correct horse battery staple.”
It also makes a reference to an actual research paper, by none other than Carnegie Mellon University – the mecca of computer science, with the same title.
That’s like if Johns Hopkins did a research project on House and somehow got it published in JAMA.
There’s actually good useful information
Ok, so some of this is fairly obvious. “Do not use common passwords, words, or phrases,” or “install an antivirus program,” (because of course you’re on Windows the immunocompromised operating system)
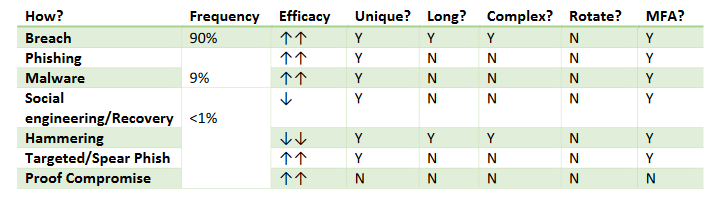
Some are less so, like the difference between phishing and spear phishing or the efficiency of social engineering. Like this:
Summary
So if you don’t have time to give this a read, here are the take-home points.
- Create a unique password for each account (duh, but also very hard to do)
- Keep your security info up to date
- Watch for suspicious activity
-
Turn on two-step verification
-
Keep your software up to date
- Be careful of suspicious emails and websites
-
Install an antivirus program on your computer
Sounds obvious? They also previously published a paper on password behaviors, and a fun little web app Telepathwords where the software tries to guess your passwords.